SharePoint Servers Hacked: Zero-Day Vulnerability Exploited
SharePoint Servers Under Siege: Zero-Day Vulnerability Exploited
Microsoft SharePoint servers are facing a critical threat as malicious actors exploit a remote code execution (RCE) vulnerability to gain unauthorized access. This vulnerability, actively targeting on-premise servers at thousands of organizations, poses a significant risk even after patching, according to security researchers. Let’s delve into the details of this alarming situation.
The ToolShell Zero-Day Vulnerability (CVE-2025-53770)
Eye Security, a European cybersecurity firm, first reported the vulnerability on July 18th. The vulnerability, now identified as CVE-2025-53770, allows attackers to bypass traditional security measures like brute-force attacks and phishing. This zero-day exploit, meaning it was previously unknown to the software vendor, gives attackers a significant advantage.
Microsoft has acknowledged the active exploitation of this vulnerability and released a security patch for SharePoint Subscription Edition and SharePoint 2019 servers. However, a patch for SharePoint 2016 servers is still pending.
Understanding the Impact
The US CISA (Cybersecurity and Infrastructure Security Agency) warns that successful exploitation of this vulnerability allows attackers to execute code remotely and gain complete access to SharePoint content. This includes sensitive internal configurations and file systems.
- Data Breach: Attackers can steal confidential documents, financial records, and other sensitive data stored on SharePoint servers.
- System Compromise: Attackers can install malware, create backdoors, and gain persistent access to the network.
- Reputational Damage: A successful attack can damage an organization’s reputation and erode customer trust.
Persistent Access: A Major Concern
Researchers highlight a particularly alarming aspect of this exploit: attackers can use stolen keys to impersonate legitimate users. This allows them to modify system components and install malicious code that persists even after security patches are applied or the systems are rebooted. This persistent access makes remediation significantly more challenging.
Global Exploitation Observed
Palo Alto Networks’ Unit 42 has reported observing “active global exploitation” of these SharePoint vulnerabilities, targeting organizations worldwide. Further details of these attacks are available on Unit 42’s GitHub threat intel repository.
Mitigation and Prevention
Microsoft strongly advises the following steps to mitigate the risk:
- Apply the July 2025 Security Updates: Install the latest security patches for your SharePoint servers as soon as they become available.
- Enable Antimalware Scan Interface (AMSI): Integrate AMSI into your SharePoint environment to detect and block malicious scripts and code.
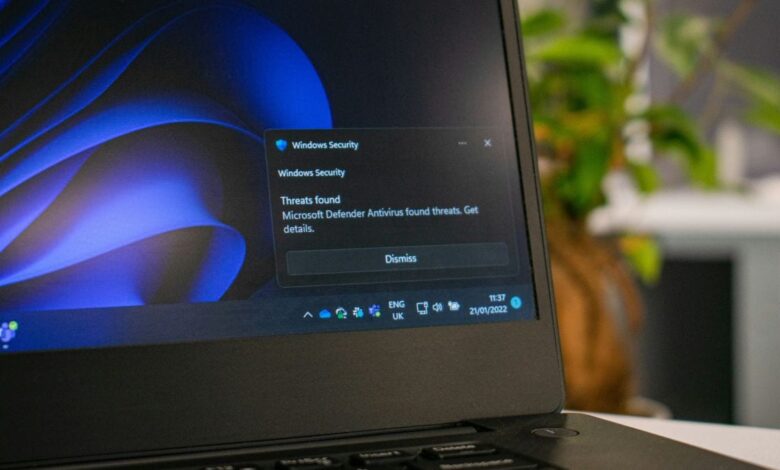
- Deploy Microsoft Defender or Similar Solutions: Implement a robust endpoint detection and response (EDR) solution to monitor your systems for suspicious activity.
The Technical Details
The CVE-2025-53770 vulnerability is a weaponized version of an exploit demonstrated at the Pwn2Own Berlin security contest. It leverages a flaw in how SharePoint handles certain types of requests, allowing attackers to inject malicious code into the server’s memory.
Analyzing the Attack Vector
Attackers typically exploit this vulnerability by sending specially crafted HTTP requests to the SharePoint server. These requests contain malicious code that is executed by the server, granting the attacker control over the system.
Post-Exploitation Activities
Once the attacker has gained access to the server, they can perform a variety of malicious activities, including:
- Installing malware
- Stealing data
- Creating new user accounts with administrative privileges
- Disrupting services
Timeline of Events
| Date | Event |
|---|---|
| July 18, 2025 | Eye Security reports the zero-day vulnerability. |
| July 20, 2025 | Microsoft acknowledges active exploitation and releases a security patch. |
Staying Protected
This zero-day vulnerability highlights the importance of proactive security measures. Organizations should regularly review their security posture, implement robust security controls, and stay informed about the latest threats and vulnerabilities. By taking these steps, organizations can significantly reduce their risk of falling victim to attacks targeting SharePoint servers.
Recommendations
- Regular Security Audits: Conduct regular security audits to identify and address potential vulnerabilities in your SharePoint environment.
- Employee Training: Train employees on how to identify and avoid phishing attacks and other social engineering tactics.
- Incident Response Plan: Develop and test an incident response plan to effectively respond to security incidents.
- Monitor Security Advisories: Stay informed about the latest security advisories and patches from Microsoft and other security vendors.